Eliminate Ransomware Risks Without Delay
Your Trusted Managed Security Service Provider (MSSP)
- Immediate Threat Detection & Response
- Proactive Ransomware Prevention
- Guaranteed Rapid Response & 24/7 Protection
- Minimize Downtime, Maximize Security
Eliminate Ransomware Risks Without Delay
Your Trusted Managed Security Service Provider (MSSP)
- Immediate Threat Detection & Response
- Proactive Ransomware Prevention
- Guaranteed Rapid Response & 24/7 Protection
- Minimize Downtime, Maximize Security

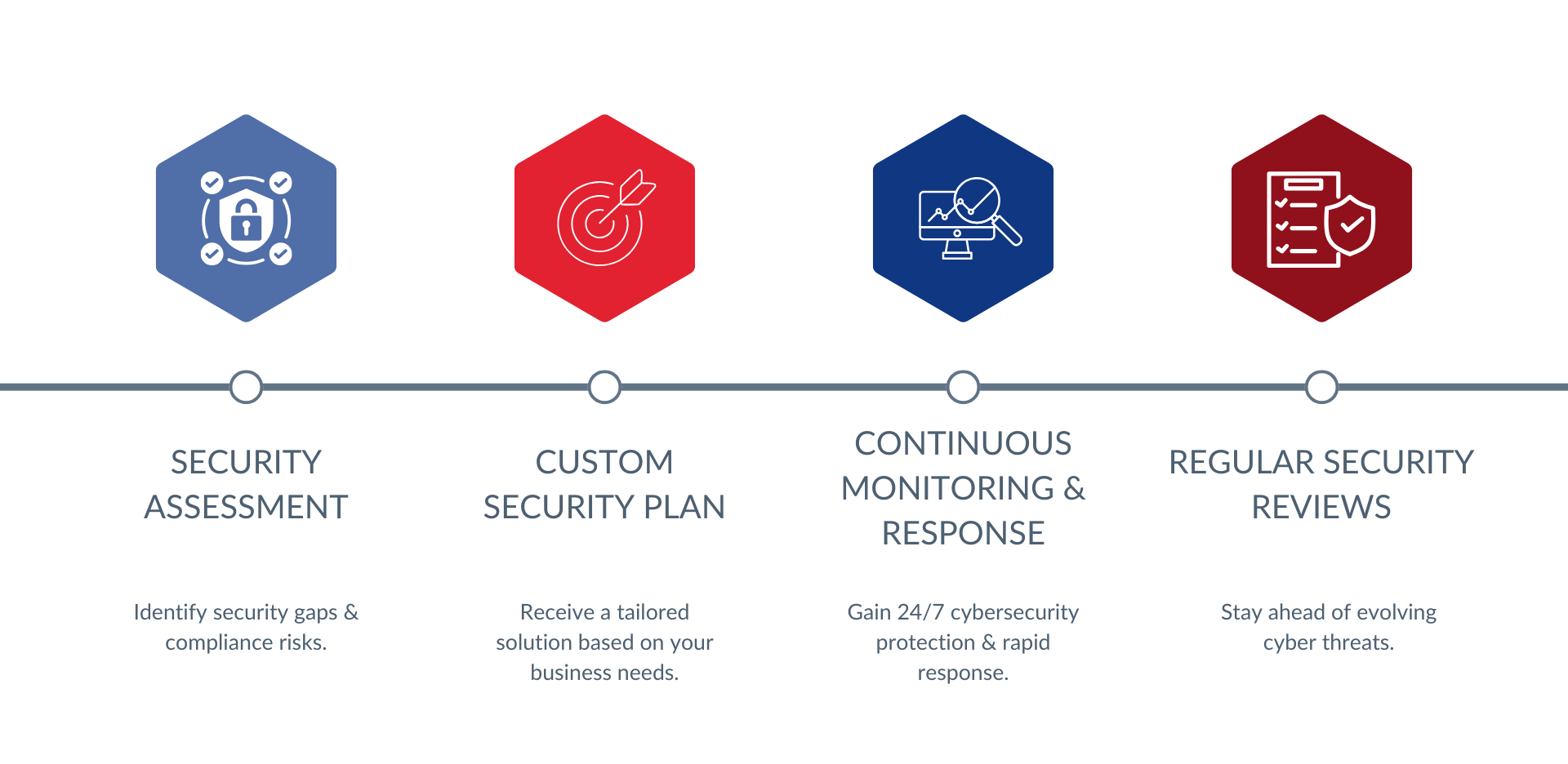
Are Hackers Targeting You?
End-to-End Cybersecurity Solutions.
Detect, Prevent, & Respond to Threats 24/7.
24/7 Threat Monitoring & SOC (Security Operations Center)
Our dedicated cybersecurity team actively monitors your network for threats.
Instantly flag and mitigate attacks with AI-powered detection.
Fast incident response ensures minimal damage to your business.
Penetration Testing & Vulnerability Assessments
Identify weak points in your systems with simulated hacker attacks.
Prevent data breaches with proactive vulnerability resolution.
Gain regular risk reports to stay informed of your security posture.
Ransomware Protection & Advanced Endpoint Security

AI-driven malware detection blocks attacks before they spread.
Ransomware prevention tools detect suspicious encryption attempts.
Secure endpoint protection for all devices—laptops, mobile phones,& servers—keeps your data safe.
Compliance & Regulatory Security
HIPAA, PCI-DSS, NIST, SOC 2 compliance audit preparation assistance.
Gap analysis & security framework implementation.
Automated security policy enforcement.
Cloud & Network Security

Cloud security for AWS, Azure, Google Cloud.
Zero Trust Architecture to eliminate unauthorized access.
Data encryption, multi-factor authentication (MFA), and firewall protection.
Our Trusted Technology Partners
We utilize best-in-class security solutions from industry leaders.
Industry-Leading Security Excellence – Recognized & Trusted Worldwide

Recognized for cybersecurity excellence.
Among the top-tier managed security providers.

We follow the highest security & compliance standards.
CASE STUDY
Streamlining the audit process & improving security posture
As part of the healthcare benefits industry, this client needed help communicating control activities and preparing for a SOC 2 audit. Miles IT’s security & compliance team conducted in-depth risk assessments and guided the client through the audit process, resulting in SOC 2 accreditation & enhanced security.

Here’s What Our Client Say About Us
“They value really good, quick response time. They get it done right the first time.”
– Dan Berger, President, Berger Rental
FAQ
-
How fast can you stop a cyberattack?
+
We provide immediate threat detection and response, with a guaranteed response time of under 1 hour. Our 24/7 Security Operations Center (SOC) ensures cyber threats are contained before they cause damage.
-
How do you protect against ransomware attacks?
+
We use AI-driven malware detection, endpoint protection, and proactive threat monitoring to block ransomware before it spreads. In the event of an attack, our rapid incident response team neutralizes threats and restores your systems.
-
Can you help us prepare for a compliance audit (HIPAA, SOC 2, PCI-DSS, etc.)?
+
Absolutely! We specialize in regulatory compliance support, helping businesses achieve and maintain SOC 2, HIPAA, PCI-DSS, and NIST 800-171 compliance, as well as other cybersecurity certifications.
-
What industries do you specialize in?
+
We provide tailored security solutions for healthcare, finance, legal, retail and any business handling sensitive data.
-
What if we already have an internal IT team?
+
We can augment your in-house IT team by providing advanced cybersecurity support, 24/7 threat monitoring, compliance guidance, and incident response—without requiring extra hires.
-
Do you require long-term contracts?
+
No! We offer flexible, month-to-month plans, so you can scale your cybersecurity services as needed—without long-term commitments.
-
How do I know if my business is at risk?
+
Cyber threats are constantly evolving, and 95% of breaches are caused by human error or outdated security. [Request a Security Assessment], and we’ll evaluate your current vulnerabilities.